6 minutes
Strategies for blocking the seven steps a fraudster's likely to take trying get inside your systems
Detecting, analyzing and preparing for the ever-increasing types of cyberattacks can be a daunting prospect for a credit union’s management team. Being told these attacks are growing in complexity and sophistication does little to lower anxiety levels. While it is true the cyber-threats we face today are more sophisticated than in prior years, it is also true we have a better understanding of the ways these attacks are carried out. Just as we use our knowledge and experiences with a member to understand better their needs, desires and goals, we can use our understanding and experiences with cyberattackers to understand better their processes, methods and ways to defend against them.
Predicated primarily by research and a paper developed by Lockheed Martin is the idea of a Cyber Intrusion Kill Chain for examining and understanding the steps taken by attackers to gain access to a network and remove data. As a chain, each link or stage is connected one to the next to the next. There are seven stages in the model: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives.
For an attacker to succeed in his or her goals, he or she needs to move through to the final, seventh stage. If the CU is able to “break the chain” at any prior point, the attacker’s plans fail. With security controls and countermeasures designed or applicable for each stage, a CU can create a layered defensive system to detect, deny, disrupt or degrade an attack.
Seven Steps Explained
During the reconnaissance step, the attacker gathers data on the target. This includes researching CU personnel and systems, reviewing its newsletters, and trolling its social media sites and postings. It can also include looking for CU information on vendor, industry association and government websites.
In the weaponization stage, the attacker uses the intelligence gathered during reconnaissance to determine how the attack will be carried out and to build the “payload.” For example, will a malicious file be sent via email or as a link to a malicious website?
The delivery stage involves getting the attack payload onto CU systems. Common delivery systems include website “drive-bys,” through which malicious code is downloaded when the user views a compromised Web page or an HTML-based email message that links to a website; malicious email attachments; malicious USB drives, dropped with the hope that someone will plug them into a computer or device; or even direct physical access (Read more about this topic).
Exploitation occurs when the delivered payload takes advantage of a vulnerability and activates. While vulnerabilities are often technical (software or hardware issues), they may also be systemic or organizational, such as poorly written policies and insufficiently trained staff.
With installation, the file or files within the malicious payload are installed, and the attacker gains a presence within the environment. This is when unwanted files become “live” within the network, such as through a botnet (a network of computers created by malware and controlled remotely), remote access or backdoor entry bypassing authentication.
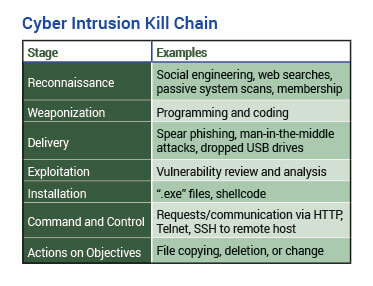
Command and control is the stage where outbound communication back to the attacker is established. With the completion of this stage, the attacker has gained access to the network and has his or her “hands in the cookie jar.”
Once the actions on objectives stage is reached, the attacker achieves his or her goals. These may include extracting or changing data, disrupting system or operations, or using the acquired access to jump to other systems or networks.
Breaking the Chain
Understanding attackers are using various resources to gather information on the CU and its personnel during the reconnaissance stage, the CU can look at ways to prevent this or minimize available information. This would include providing employees training on social engineering attacks; development and use of a data classification security schema to minimize the release of confidential or privileged information; and creating an understanding within the organization that neither the CU’s size, type nor location are protections against attackers. From a technical perspective, network intrusion detection and network intrusion prevention systems and firewalls come into play.
While weaponization takes place “offline” and isn’t something directly seen or felt by the credit union, understanding the process is important. Attackers weaponize payloads by understanding the systems (hardware and software) in use and the vulnerabilities of those systems. For the credit union, defenses in this stage would include maintaining inventories of hardware and software used in the credit union; assessing the criticality of the systems and the level of sensitivity of any data stored on them; and ensuring that knowledge of system vulnerabilities is transferred to appropriate personnel.
For the delivery stage, the attack moves into areas and defenses generally more familiar to the credit union. Defenses here would include web and email traffic proxy filters; in-line email anti-virus scanning and spam filtering. In this stage, employee security training, particularly regarding phishing attempts, also comes into play.
To counter exploitation, the CU needs to limit the vulnerabilities on its systems and the ability of the malicious payload to execute. The primary way to limit system vulnerabilities is through continuous patching and keeping operating systems and software current. The ability for malicious software to do damage can also be limited with the use of host-based intrusion detection systems (which monitor the internals of a computing system); data execution prevention (which marks areas of memory as either “executable” or “nonexecutable,” and allows only “executable” data to run); and software white-listing (registration provided a particular privilege, service, mobility, access or recognition).
For installation, the CU is looking to stop the creation of new files on systems, or the replacement of existing files with malicious versions. Defenses for this include system (PC, server, device) anti-virus packages; host-based intrusion detection systems; and limiting user administrative privileges often needed to install or update files or software.
At the command and control stage, the CU is looking to deploy defenses against outbound traffic. Defenses deployable here are similar to those used to prevent in-bound attack traffic—just turned around. For example, firewall access rules can deny outbound traffic, and network intrusion detection and prevention systems can scan network segments.
For the actions on objective stage, the defenses the CU has deployed have failed to stop attackers. As one security consultant has put it, “At this point, the fire is burning in the office, and your hope now is to limit and control the damage.”
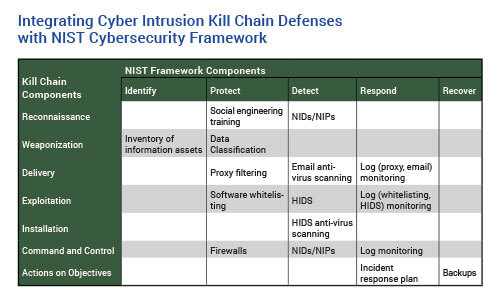
The table at left provides examples of how the various discussed defenses can integrate into the NIST Cybersecurity Framework.
In reviewing, analyzing and determining how the information in this article can be integrated into the credit union's cybersecurity program, it is important this process not be viewed as a one-time exercise. As the credit union gathers intelligence on attacks against themselves or others, this threat intelligence should be matched against the kill chain stages and current defenses. And just as the credit union uses data gathered on loan approvals, rejections, delinquencies and charge-offs to analyze and update its loan program, threat intelligence gained from attacks should be used to analyze, refine and update cybersecurity defenses.
Jim Benlein, CISA, CISM, CRISC, owner of KGS Consulting, LLC, Silverdale, Wash., offers insights to CUs on information technology governance, information security and technology risk management.